Public WiFi Security: 8 Essential Tips
Public WiFi zones provide internet access in cafés, restaurants, hotels, hopping malls, beaches and parks, as well as on trains and buses. In most cases, this service is even free of charge. Still, this practical alternative for devices without a SIM card, or to conserve a mobile phone contract’s s remaining data volume involves from precautions. You can find out what to pay particular attention to below.
Table of Contents
What are the risks associated with public WiFi?
There are numerous dangers lurking in public WiFi zones. In theory, you would expect the WiFi operator to offer its users a secure environment; unfortunately, however, that is not always the case. Moreover, hackers are always able to exploit even the smallest security gaps to gain access to your data. These are the most common dangers:
Unencrypted WiFi
When using WiFi with no encryption, your activities are like an open book. Depending on your device and operating system, you receive information about whether and which encryption is set up when you log in. If access is gained without a WiFi network key, the connection is unencrypted and therefore very insecure. In fact, this is often the case in public WiFi, even if you have to log in or register on a homepage.
Man-in-the-middle attack (MITM-attack)
Man-in-the-middle attacks are very widespread. In simple terms, this involves someone getting between your device and the services or websites you contact. In the past, this type of attack was most often carried out by physically accessing data streams, but today eavesdropping attacks by constructive means predominate. The tools for this are available on the Internet and are so sophisticated that even less experienced criminal users can exploit security gaps to their attacks.
The insidious thing is that an MITM attack not only makes it possible to observe your surfing behaviour and read your communication, password, and form entries. Cyber criminals can also actively intervene and manipulate the data you enter before it reaches its target.
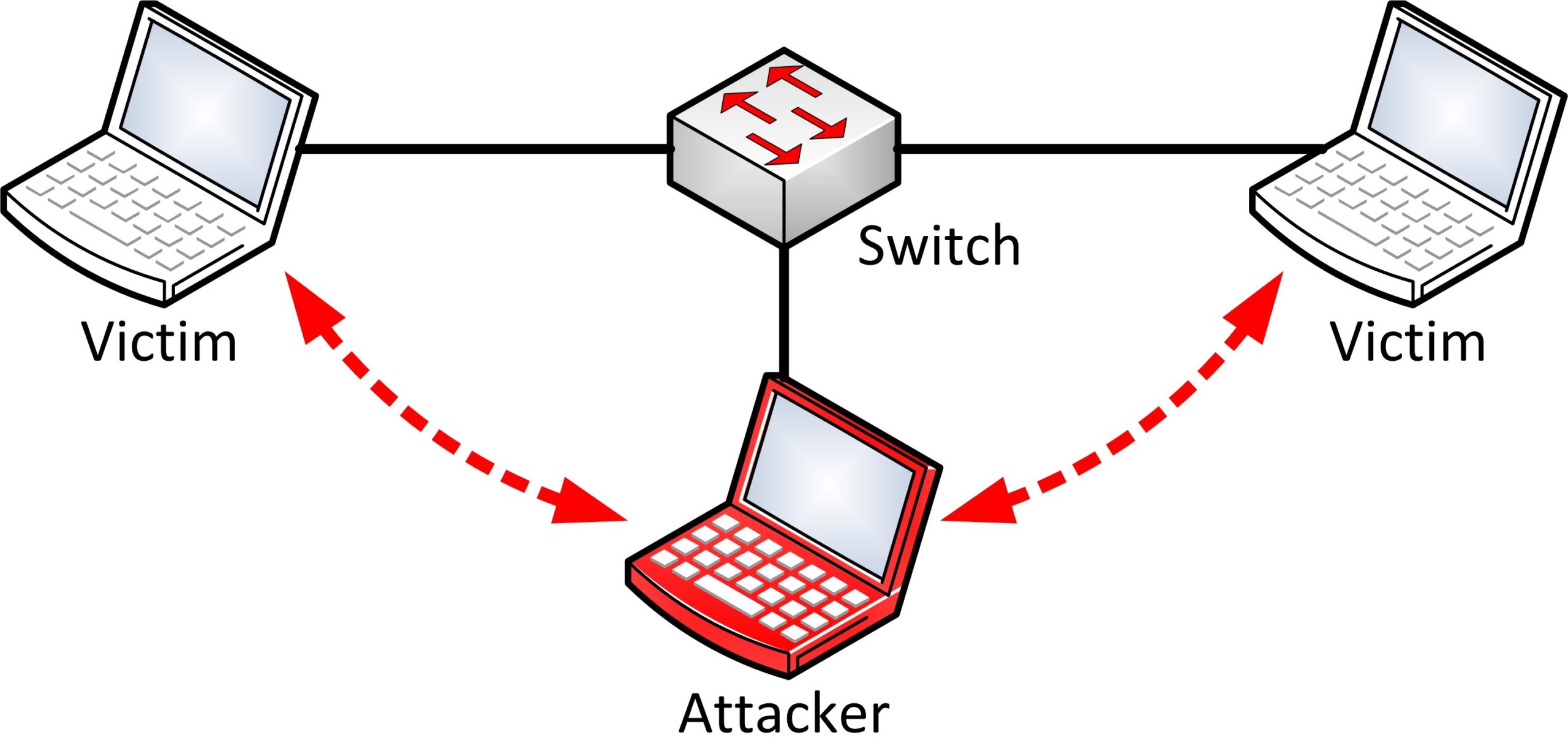
MITM attacks are especially dangerous if you’re on a public network and using software that doesn’t rely on end-to-end encryption. (Image: Nasanbuyn)
Snooping and Sniffing
Another method of interference in WiFi is snooping or sniffing. This involves spying on your Internet activities via WiFi signal to and form an Internet access point. The devices and programs required for this are freely available and allow snooping or sniffing on your entries, for example, to gain access to your accounts.
Malicious hotspots
Every access point within your range has a name that the operator can freely assign. This makes it easy to set up a malicious hotspot and name it after a trusted location in the immediate vicinity. For example, you find a free Internet access point with the name “CappuccinoHeaven Free WiFi” in a café called “CappuccinoHeaven”. Assuming that this is the café’s public WiFi, you log in.
In reality, you have connected to a cyber criminal’s network who can now spy on you.

When it comes to hotspots, what you see is not always what you get.
Malware distribution
If hackers manage to get into your smartphone, laptop or tablet due to security gaps, it not only gives them opportunities to read and manipulate your information, they can also install undetectable malware on your device which gives them permanent access to your system.
How do I know if I am on a public Wi-Fi network?
Almost all WLAN-enabled devices have a WiFi connection status display. If a connection is active, you can also find out the name of the access point here. This can be your router at home, the access point at work, or a hotspot via your mobile device. However, if it is a name of a public place like a restaurant or a recreational facility, you can assume that you are in a public WiFi zone.
What should I do to browse safely on a public WiFi?
Attacks in public WiFi zones happen more frequently than one would assume. What’s more, they can cause a great deal of damage with comparatively little risk to cyber-criminals. Fortunately, there are a number of ways you can protect yourself on public WiFi networks.
Set up a VPN
You can benefit from a very high level of security just by using a VPN (Virtual Private Network) in the public WiFi zone. Basically, a VPN is a service that virtually routes you to a server in another location. On the way there, your data is encrypted in such a way that it is not visible to potential hackers. This is why it is called a VPN tunnel.
The data can only be used again when forwarded from the VPN server and provided with its IP address. This has the additional advantage of disguising your actual location or device location to protect your privacy.
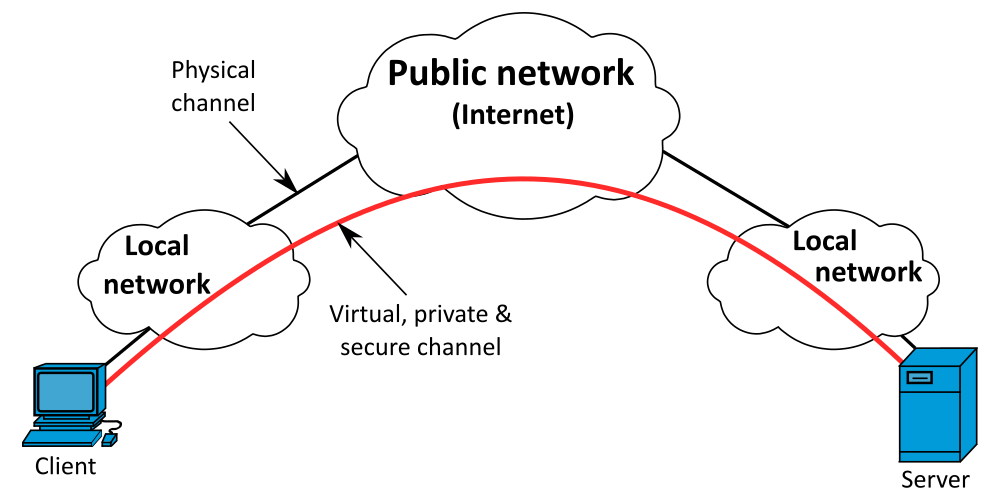
If you use a VPN, your data is encrypted and your security on a public WiFi increases dramatically.
(Image: Michel Bakni)
VPN solutions come in different variations. There are standalone apps, where you can often choose between a free service with stripped-down performance and security, or a paid model. Also, most security and antivirus packages offer an integrated or separate VPN service. Alternatively, you can set up your own VPN, provided you have the appropriate skills.
Depending on the configuration, your equipment and security devices at home or work serve as the target server for the VPN tunnel.
Antivirus programs: a must-have
A reliable antivirus program is a necessity for all Windows, Android and iOS systems. It protects you from malware in the form of viruses, Trojans, spyware and the like. However, you should make sure that you always use the latest version of your chosen program. If the program detects a possible attack, you will often receive a warning accompanied by various alternative actions.
Many antivirus programs automatically offer comprehensive protection in their free versions. However, you usually have to pay a fee to benefit from the full range of service. You can save money here by opting for offers that often cover even multiple devices across operating systems.
Disable file and folder sharing
Many public WiFi networks are configured so that the connected devices are visible within the network. If this is the case, other participants can access shared areas of your device. So before you log into a public network, you should disable all file and folder sharing.
Windows 10, for example, also lets you device whether you are on a public or private network. Select “Public network” to limit your visibility by default.
Disable automatic WiFi connection
Most WiFi-enabled devices can be set to automatically connect as soon as there is a strong enough signal. With this option, you avoid having to manually re-login your smartphone, tablet, or similar device every time you move from one hotspot to the next. On the other hand, you give up control over where you log in. This makes it possible to connect to an unstable or even malicious network. To be on the safe side, you should disable the automatic WiFi connection.
By the way: smartphones and other mobile-capable devices almost always have the option of automatically switching from mobile date traffic to WiFi when available. You should deactivate this as well.
Opt for encrypted networks
Internet access that is encrypted according to the WPA or WPA2 standard generally offers higher security. This is therefore also the first choice for public WiFi. However, if unencrypted WiFi is the only thing available, at least make sure there is a verifiable login or registration process.
Maintain caution while banking and shopping online
When you bank online, you share a lot of sensitive information. This includes access codes, account data and insights into financial transactions. This is only recommended if the highest security standards are in place. You should therefore avoid online banking in unencrypted WiFi zones. Still, special caution is also advisable for encrypted networks. First of all, you should be sure that you are not connected to a fake network. It’s best to additionally secure your device with a VPN when banking online. Also, make sure that non one has the opportunity to view your entries for, example, by looking over your shoulder.

Admittedly, verifying transactions using mTAN can sometimes be annoying, but it also noticeably increases security for critical transactions, such as online banking. (Image: Christian Wiediger)
Similar security measures are also required when shopping online. Numerous providers offer you the option of additional security via a mobile transaction authentication number (2FA) for both banking and shopping. For each transaction, you receive a security code via secondary channel that you specify in advance. For example, while you are making a transfer or a purchase online on your tablet, a verification code is sent to your smartphone. Without it, you can’t confirm your action. So if someone has hijacked your account, at least they won’t be able to make transactions—unless they also have access to your mobile phone.
Don’t leave devices unattended
Obviously, if you are in a public area, you should not leave your devices unattended. A few seconds are long enough to capture screen content. Therefor, set up reliable screen locks.
Delete known networks
It is just as important to delete connection data of visited public networks after logging out as it is to prevent an automatic WiFi connection. You will have to enter them again when you access the network later. However, it makes sense to do so because cyber criminals can easily set up a malicious hotpot with connection information that is identical to any data you may have saved.
Conclusion
As convenient as public WiFi networks are, they are rife with rusk. However, the use of a VPN and an up-to-date antivirus program, as well as a few precautionary measures, can protect you effectively. It’s a small effort that pays off.

